Required customer Function Modules
To use the full potential of the Performer Suite, please install all function modules.
👉🏽 The Performer Suite allows you to install and update all necessary function modules in your SAP system automatically and with minimal manual effort.
The scope of functions can be extended by using those RFC-capable customer function modules.
(with BW releases from 7.4, it is necessary to use customer function modules for SAP synchronization)
Documentation:
Overview of customer Function Modules
# | Module | Function Module | Current Version | Description |
1 | General | Z_RFC_ENTITY_SYNC | 1_9 | Synchronization with SAP objects. If the Function Module is not installed, the synchronization works, but with less performance. |
2 | Docu Performer, | Z_RFC_READ_REPORT | 1_0 | Read the Source code of Includes, Reports, and Function Modules. |
3 | Docu Performer | Z_RFC_GET_DTP_DETAILS | 1_4 | Read DTP Filter and Semantic Groups. |
4 | Docu Performer | Z_RFC_AUTH_CHECK | 1_1 | Identify users who are authorized to Queries. If the Function Module is not installed, this will still work, but with much less performance. |
5 | System Scout | Z_RFC_USAGE_ANALYSIS | 2_0 | Mandatory for Where-Used analysis of InfoObjects and reporting entities. The Where-Used analysis of InfoProvider works also without the Function Module. |
6 | System Scout | Z_RFC_CODESCAN | 2_2 | Mandatory for a scan of ABAP source code (coding in Transformations, Includes, Methods, DTP Routines, etc.) |
7 | Docu Performer, Migration Booster | Z_RFC_GET_STRING | 1_8 | Mandatory for table calls where at least one field is of type STRING. |
8 | Migration Booster, | Z_RFC_TRANSLATION | 1_2 | Change descriptions of objects in relevant tables of the SAP BW-System. |
9 | Migration Booster | Z_RFC_ADSO_GETDTL_XML | 1_1 | Read information about an ADSO. |
10 | Migration Booster | Z_RFC_ADSO_CREATE_XML | 1_2 | Create and activate ADSOs in the SAP BW-System. |
11 | General | Z_RFC_FUNCTION_DELETE | 1_0 | Delete Function Modules in the SAP BW-System. Required when updating Function Modules. |
12 | Translation Steward | Z_RFC_CHECK_ACT_TR | 1_1 | Check, activate, and assign transports of all object types in the Translation Steward. |
13 | Migration Booster | Z_RFC_HCPR_CREATE | 1_0 | Create and activate HCPRs in the SAP BW-System. |
The first character (by default: 'Z_') is a freely selectable prefix that can be defined individually.
Keep in mind, the SAP function module "FUNCTION_CREATE_REMOTE" does not support technical names containing a slash '/'.
If you really need this character (because of own SAP customer namespace), we recommend the following:
👉🏽 Simply create the function module with Z_ and then copy it to the required namespace in SAP.
TOP-Include (manual creation)
If your company policy does not allow the automatic installation of function modules via the Performer Suite, you can install them manually.
In this case, the TOP include must also be modified (see code below):
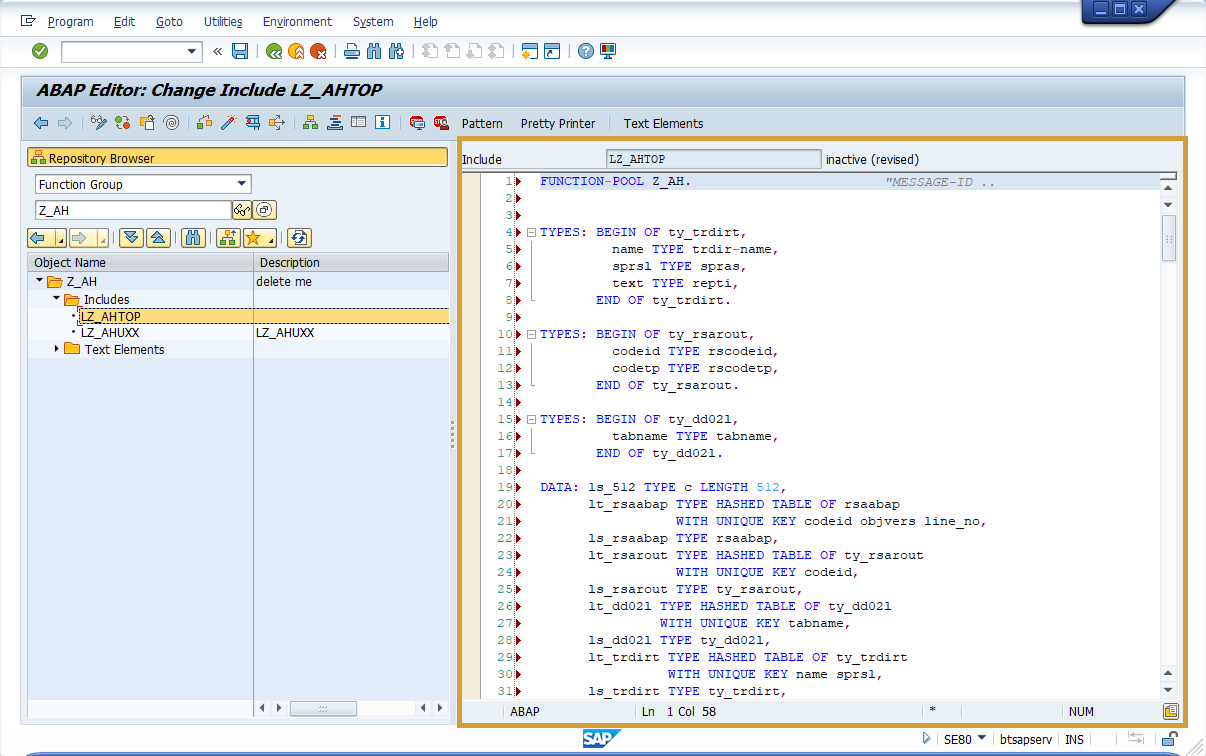
👉🏽 Replace Z_AH in our example below with the name of your function group.
Required Authorizations in SAP
You need the following SAP authorizations if you want to install the customer function modules:
AAAB - Cross-application Authorization Objects
S_RFC - Authorization Check for RFC Access [T-B274007000]
Authorizations Field | Values |
ACTVT | 16 Execute |
RFC_NAME | AUTHORITY_CHECK, ENQUEUE_READ, RFC_FUNCTION_DELETE, RFC_GET_ FUNCTION_INTERFACE, RFC_READ_REPORT, RFC_READ_TABLE, RFC1, RFCPING, RPY_INCLUDE_UPDATE, RS_FUNCTION_POOL_INSERT, RS_FUNCTI- ONMODULE_INSERT, SDTX, SEUF, SIFP, SIW_RFC_REPOSITORY, SIW_RFC_WRI- TE_TADIR, SUNI, SUSR, SYST, USER_NAME_GET, Y*, Z* |
RFC_TYPE | FUGR, FUNC |
S_SIW_CFG - Authorization for projects in SIW [T-B274007000]
Authorizations Field | Values |
ACTVT | 02 |
Config ID | <DUMMY> |
BC_A - Basis: Administration
S_TABU_NAM - Table Access by Generic Standard Tools [T-B274007000]
Authorizations Field | Values |
ACTVT | 03 |
Table | CVERS, DEVACCESS, E070V, E071, FUPARAREF, INFO_FUNCT, PROGDIR, TADIR, TFDIR, TLIBG |
BC_C - Basis - Entwicklungsumgebung
S_DEVELOP - ABAP Workbench [T-B274007000]
Authorizations Field | Values |
ACTVT | 01, 02, 03, 07, 16 Execute |
DEVCLASS | $TMP, *, Y*, Z* |
OBJNAME 1 | Y*, Z* |
OBJTYPE | FUNGR, FUNC |
P_ GROUP | * |
For "DEVCLASS" and "OBJNAME" customer-specific namespaces are required.
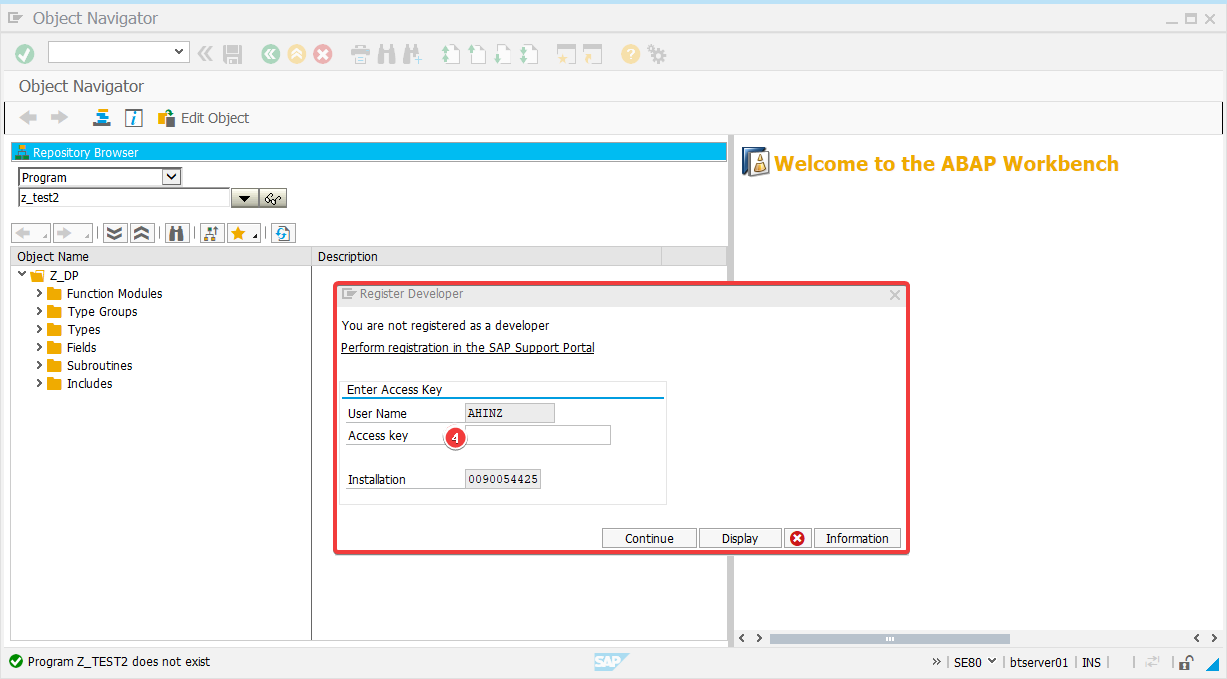
Developer Key
For a Dev Key, please check the table DEVACCESS (SAP transaction SE16) for your user name to be found.
The SAP user needs a Developer Key (from your SAP Basis) in the following two cases:
If you want to create new Function Modules or
Update present Function Modules (e.g. after a major release of the Performer Suite)
Onwards SAP Basis Release >= 7.53 (table=CVERS /COMPONENT=SAP_BASIS), we no longer need to check for a developer key (when we create the function modules).
As of SAP Basis 7.53, the authorization object S_DEVELOP is required.
BW/4HANA 2.0 and certain releases of S/4 are then based on an SAP Basis >= 7.53.
If your SAP User cannot be found in the table DEVACCESS, but you received a Dev Key from your SAP basis do the following:
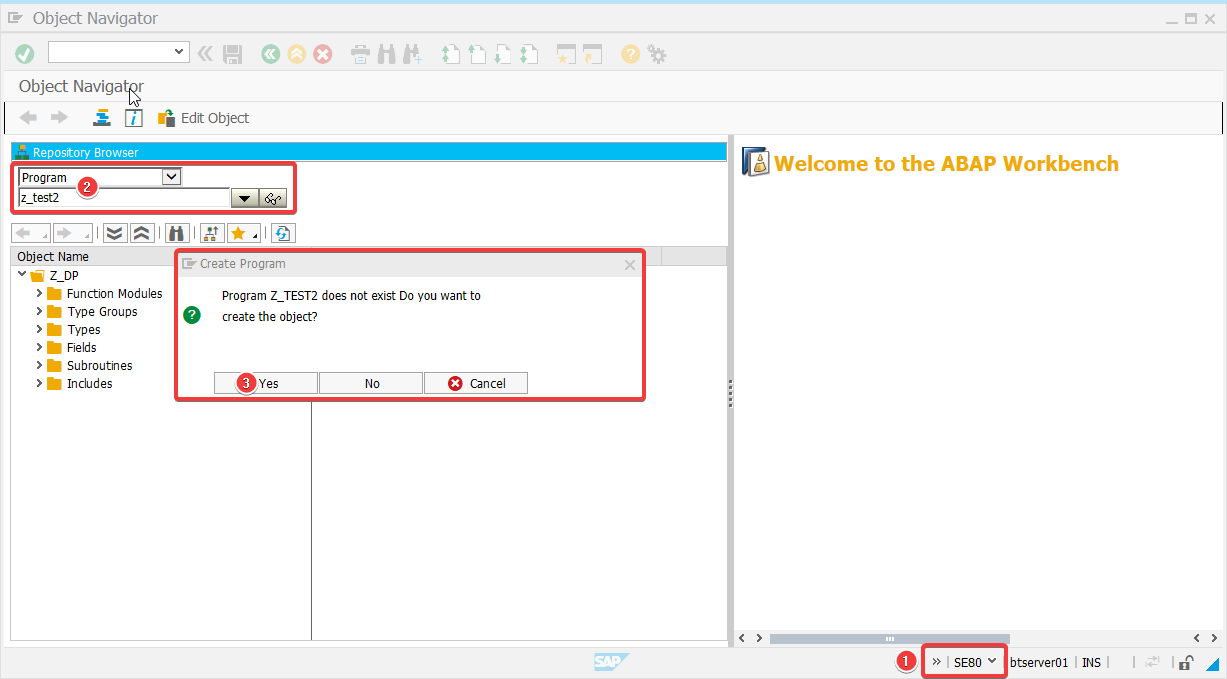
Go to SAP transaction SE80 and start creating a program.
Proceed with the process, until the SAP GUI asks you to enter your Developer Key.
Now, the check of the Function Modules will be successful (no need to restart the Performer Suite).